Abo ut
About us
Since 2005, our business unit Identity and Security Management has been supporting medium-sized and large, internationally active corporations and public institutions in the planning, implementation and maintenance of sophisticated solutions for user and authorization management, smart card management and strong authentication.
The basis for our solutions is a carefully selected portfolio of high-performance product platforms, which we tailor precisely to the respective requirements in the company in close cooperation with our customers and which we integrate into overall end-to-end solutions.
Our solutions have a major impact on the efficiency and security in the company. We respond to this challenge with the use of highly qualified employees, the development of expert knowledge and a methodical way of working.
A large number of satisfied customers from different industries serve us as references and confirm the quality of our solutions and services.
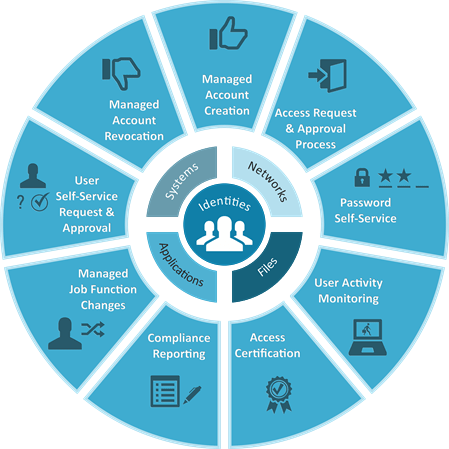
User and authorization management
Transparency and efficiency for administration processes
Employees, partners, suppliers and customers today need access to a wide range of IT resources, such as networks, databases and application systems. With our solutions for user and authorization management, you can manage the identity data, accounts and access rights of individual users across systems from the day they are created until they leave the company. With the right combination of workflows, guidelines, synchronization mechanisms, provision and cancellation procedures, role management and user self-services, we help you to improve the efficiency of your administration processes while minimizing the risks of manual activities. Reporting, auditing and attestation functions also ensure that your compliance requirements are better met.
Our solutions for user and authorization management are based on the NetIQ Identity Manager from Micro Focus and the One Identity Manager from Quest. Extensive functionality and top performance characterize these products. We would be happy to provide you with detailed information on how we can use this to implement even the very complex requirements of your company in terms of user and authorization management.
Strong authentication
Protect IT systems from unauthorized access
Those who want to reliably protect their IT systems from unauthorized access today can no longer avoid using strong authentication methods! Whether with a smart card, USB token, one-time password or SD card: We offer you the right solutions for strong authentication, including the necessary middleware and public key infrastructure (PKI). We emphasize a particular importance to the central management of user credentials and the seamless integration of the solution into your existing IT environment.
And: In conjunction with single sign-on, daily access to the multitude of IT systems can also be designed to be user-friendly. After logging into the system only once, the user can quickly and personalized access to all applications, services and information relevant to his work. In this case, the authentication of the user to the individual IT systems is done by the single sign-on mechanism.
Our solutions for strong authentication and single sign-on are based on technologies and components from Microsoft, Cryptovision, Nexus, Entrust, Gemalto, Siemens, Evidian, and others.
As a manufacturer-independent provider, we would be happy to explain the various options that you have to implement strong authentication in your company and we will discuss the respective advantages and disadvantages of the different approaches with you. Our specialists will be happy to provide you with further details.
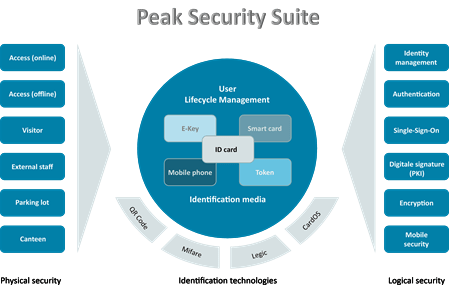
Smart card management
Manage multifunctional ID media across all applications
ID media - such as chip cards, USB tokens or NFC cell phones - are the key to a growing number of applications today. For example, they have established themselves as contact-free readable ID for access control as well as a secure storage medium for digital certificates for the authentication of IT users and the encryption of data.
With our solutions for smart card management, we enable you to manage multifunctional ID media across all applications. We support all important coding processes: Both for contact-based chip cards, e.g. based on STARCOS, CARDOS or JavaCards, as well as for contactless chip cards, e.g. based on LEGIC prime and advant, MIFARE classic and DESFire or HITAG, HID Prox or iCLASS.
Our solutions can be easily integrated into existing system landscapes and communicate via standardized connectors with various applications from the human resource environment (e.g. SAP), time + access (e.g. dormakaba, Primion, Interflex, nedap), canteen (e.g. CashControl POS systems, Seitz machines) , Public Key Infrastructure (e.g. Microsoft, Nexus) and Identity Management (e.g. Micro Focus, Quest).
Freely definable print layouts allow you to create different types of badges for different user groups, such as employees, visitors or customers. The individually adaptable processing workflows and security guidelines make the subsequent management of the multifunctional chip cards safe and efficient.
With our product Peak Security Suite, we have a platform on the basis of which we can also implement very demanding tasks in the field of smart card management in a future-proof manner.
From planning to successful application
We offer you an extensive range of professional services so that your company can take full advantage of modern solutions for user and authorization management, smart card management and strong authentication.
- On the basis of our vendor-neutral maturity analysis, we work with you to identify the potential for process improvements in an understandable and structured way.
- As part of a tool-supported authorization analysis, we examine your IT landscape specifically for unused accounts, unassignable IDs, users with privileged authorizations and members of administrative groups and, if necessary, clean up the "grown" structures on the basis of coordinated guidelines.
- With the help of our proven IAM project methodology, various reference models from practice and numerous templates, we accompany you systematically and efficiently in the description of your processes, the specification of your requirements, the selection of a suitable solution platform and the development of technical concepts.
- With our experienced project managers, business consultants and certified product specialists, we support you professionally in the implementation of your solution and, if necessary, bridge resource bottlenecks in your project.
- On the basis of defined service levels, we offer you comprehensive support and maintenance services and ensure the ongoing development of your solution.
We would be happy to provide you with detailed information about our diverse range of services in a personal meeting.
4 Sprungmarke
Find out more
Download (pdf) of the technical article: Consolidation security concepts - Against the administrative wild growth in security - (German)