Abo ut
Comprehensive process control for heterogeneous access control landscapes
With a comprehensive IAM system (Identity and Access Management), the provision and withdrawal of IT rights for different user groups can be designed transparently and efficiently. But IAM systems quickly reach their limits when systems for physical access control are to be integrated. Because when it comes to managing access rights for opening doors, different criteria come into play than when managing IT rights.
Usually, the authorization objects of physical access control systems are defined using room zones and time profiles. In addition, they may be subject to short-term changes, for example if access to rooms or storage areas has to be restricted due to a sensitive order. In addition, access rights are often given time restrictions, e.g. for the duration of a certain project. Another complexity arises from the combination of rights with special evidence - for example, the binding of access rights to evidence that a safety briefing has been completed or updated.
The examples mentioned make it clear: Requirements towards physical security do not coincide with those of logical security. They are alien for the provisioning systems commonly used.
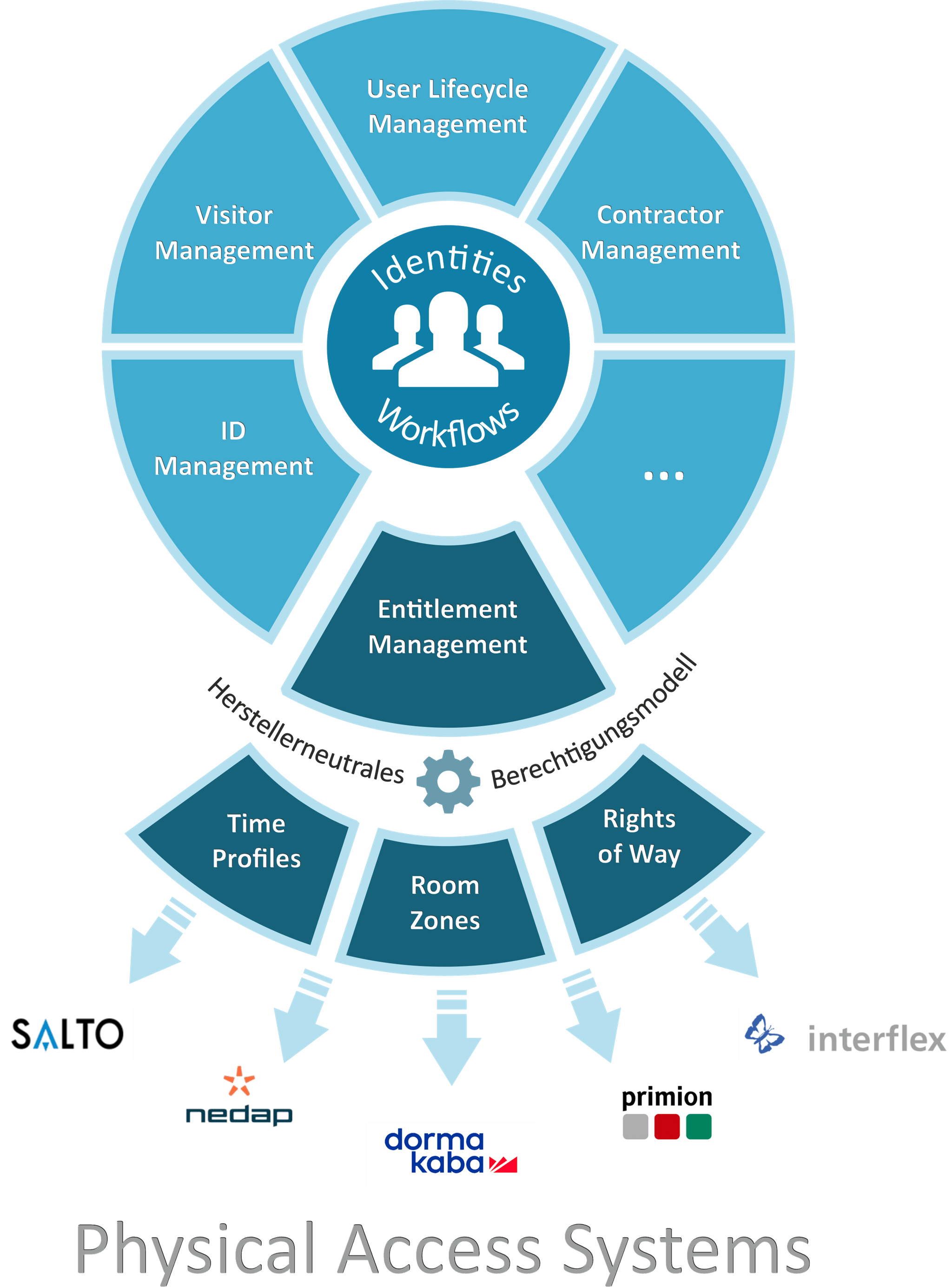
It becomes really demanding when access control systems from different manufacturers are in use at distributed locations. This can become an urgent problem with a company takeover, for example. The question then is: should the locking systems of the new building complexes be exchanged for a lot of money just to get a uniform access control system again?
It is better to combine the different access solutions in a meta system. One such meta system is the Peak Security Suite. One of its core components is the central administration and workflow-based assignment of access profiles for different access control systems (= Entitlement Management).
Since the different access solutions differ conceptually with regard to the mapping of access profiles, the Peak Security Suite implements a higher-level, manufacturer-neutral authorization model. Any authorization objects can be defined in it, which can be combined very flexibly into logical access profiles using a sophisticated process - taking into account room zones, walking routes and time profiles. The logical access profiles are then resolved system-specifically by the Peak Security Suite and provisioned in the respective end system via micro services.
In this way, a uniform, cross-system management system for access profiles can also be implemented for a heterogeneous access control landscape. The service-oriented architecture of the Peak Security Suite and its implementation as secure cloud services are particularly advantageous for connecting distributed locations. In addition, with the help of further components, e.g. for badge management, visitor management, user lifecycle management, external company management, etc., the solution can extend the range of functions of the existing access control systems across all systems.
